Selecting the Right Key Offering in Azure for Optimal Security
Written on
Chapter 1: Understanding Azure Key Management
In today's digital landscape, safeguarding data is paramount for businesses, particularly those that rely on critical applications. It's essential to grasp how to protect data and manage its lifecycle effectively in a cloud environment.
Azure offers two primary types of encryption keys: Platform Managed Keys (PMK) and Customer Managed Keys (CMK). PMKs are generated, stored, and maintained by Microsoft, giving customers no control over them. For most Azure services like Azure Disk and Storage Accounts, these keys automatically encrypt data at rest without incurring additional costs.
Conversely, CMKs allow customers to manage and oversee their keys based on the specific offerings available. These keys can be further categorized into software-backed and hardware-backed keys, providing organizations with various options to tailor their encryption strategies to meet specific use cases.
The choice between PMK and CMK affects factors such as FIPS compliance, administrative workload, and the complexity of key management. The following comparison highlights these differences:
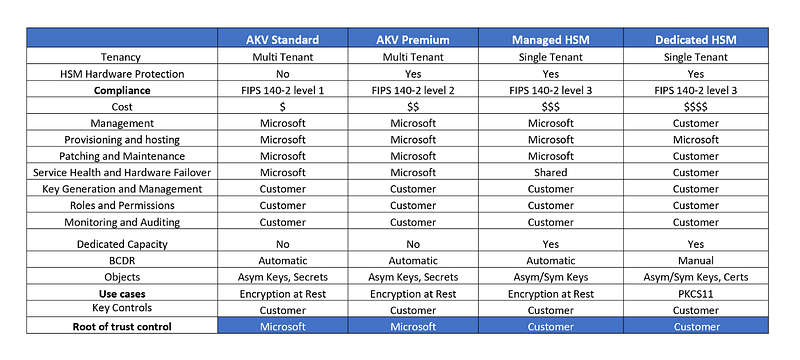
Photo by Author ©
The most utilized key management service within Azure is Azure Key Vault (AKV). This service is validated under FIPS 140–2 Level 1 and serves as a multi-tenant cloud key management solution. Besides storing encryption keys, AKV can also securely hold secrets and certificates. The keys managed by Azure Key Vault are software-protected, employing RSA and AES algorithms, making it a cost-effective choice for applications that do not handle personally identifiable information.
Azure’s encryption at rest employs a method known as envelope encryption, which secures a Data Encryption Key (DEK) with a Key Encryption Key (KEK).
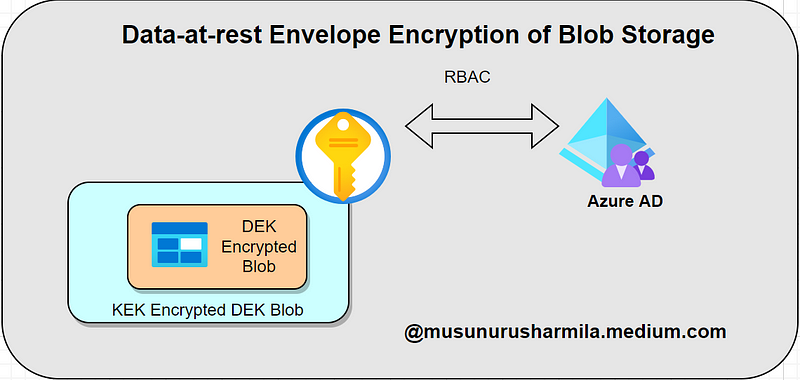
Photo by Author ©
Data Encryption Key (DEK): This is a symmetric AES256 key used to encrypt data blocks or partitions. Each data block can be secured with a distinct DEK, complicating any potential cryptographic attacks.
Key Encryption Key (KEK): This key is responsible for wrapping or encrypting the DEKs through envelope encryption. The DEKs can be encrypted and managed using a KEK that remains within the vault. Customers can securely delete DEKs and other sensitive data since the KEK is required for decoding the DEKs.
Azure Key Vault (Premium Tier): This is a FIPS 140–2 Level 2 validated offering that uses Hardware Security Modules (HSM) to store keys within a secure environment managed by Microsoft. It is ideal for scenarios where users need KEK keys secured by HSM but prefer not to manage HSM in the cloud.
Azure Managed HSM: This single-tenant HSM product has achieved FIPS 140–2 Level 3 validation, providing users with complete control over HSM for encryption-at-rest, Keyless SSL, and customized applications. Microsoft manages provisioning, maintenance, and failover of the HSMs, but does not have access to the keys since the service operates in a secure environment.
Azure Dedicated HSM: This service offers a single-tenant FIPS 140–2 Level 3 HSM, where customers can lease HSM hardware located in Microsoft data centers. The device is fully owned by the customer, who is responsible for firmware updates and security. This service is particularly suitable for traditional workloads and integrations with various platforms such as F5 and Nginx.
Stay connected for more insights and updates. If you found this article valuable, please share your thoughts to support my work!
If you're interested in deeper insights, consider joining Medium with my discounted referral link. Additionally, if you'd like to support my writing, feel free to buy me a coffee.
Chapter 2: Key Management Strategies and Resources
In this section, we will delve into effective strategies for managing keys in Azure, focusing on best practices and resource optimization.
The first video, "Partitioning: Choosing the Right Key for Cost and Performance with Azure Cosmos DB," provides insights into selecting the appropriate partitioning strategy to optimize cost and performance in Azure.
The second video, "Creating an Azure Key Vault Step by Step," walks through the process of setting up Azure Key Vault, offering practical guidance for effective key management.

Photo by Author ©